After reading the Rust book and writing about my initial experiences, I wanted a small practical project to familiarize myself with the language. So, I decided to write a REST client library. This post shows, step-by-step, how my initial design was refactored to be more robust and easy-to-use. Traits and generics are key concepts in these refactorings. The intent is not to cover the internals of the library in detail and also the basic syntax of traits and generics is not covered here. The Rust Book chapter 10 is an excellent resource for the latter.
Programming fonts with ligatures
For long, there have been fonts that are specifically designed for programming. Usually the main characteristics of these fonts are clear and easy to read characters (especially i, I, 1, o, O and 0), easily distinguishable brackets, quotes and parentheses and emphasized punctuations. This design is done with the font’s typeface. Now there are also fonts that, in addition, introduce special ligatures specifically for coding. Continue reading “Programming fonts with ligatures”
My experiences learning Rust
Having seen a lot of positive buzz around the Rust language, I decided to look into it myself aswell. So, past couple of weeks I have been reading the second edition of The Rust Programming Language book which is an introductory to the language. This blog post is a round-up of my first impressions about the language and its features, and it also serves as a quick intro for others interested in it. In my day job I work mostly with C and C++ so those are my main reference points when learning a new language. Continue reading “My experiences learning Rust”
How to flash Sonoff S20 WiFi outlet with Tasmota MQTT firmware
Sonoff S20 (specs) is a smart power outlet that is controllable with a WiFi connection. The device comes with a built-in firmware and an accompanied mobile app, but it is also possible to flash it with custom firmware. This allows to control the device with standard MQTT protocol making integration to DIY home automation or IoT cloud systems easier. This post provides a step-by-step guide how to flash the device and also examples how to interface with it using MQTT. Continue reading “How to flash Sonoff S20 WiFi outlet with Tasmota MQTT firmware”
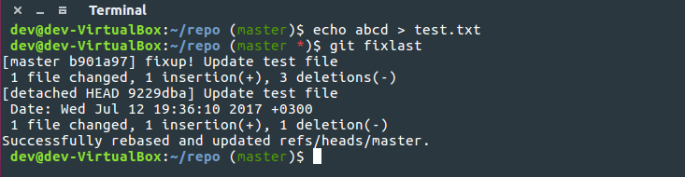
Git: easily auto-squash changes to previous commit
After committing, I always like to go through the diff before pushing the changes upstream. Just to make sure that everything is as it should be. Well, quite often I still spot some typos, commented out code that I was supposed to remove or some other minor things that need to be fixed. So I ended up running the same exact commands time and time again. First new commit for the fixes and then interactive rebase to squash the changes to the previous commit. Perfect opportunity to make an alias to save those precious keystrokes. Continue reading “Git: easily auto-squash changes to previous commit”
Don’t build one to throw away, iterate
I recently read the Mythical Man-Month, a collection of essays on software engineering by Frederick Brooks. He writes about his observations and experiences from working at IBM and managing the OS/360 project in the sixties. The book was first published in the 1975 which, I have to say, shows in the examples. Many parts feel a bit dated now (like the discussion how to do time-allocation on a central computer). Still, if you look past the old technical references the essays contain a lot of good general guidelines and observations that are still relevant today.
One of the essays that especially caught my attention was “Plan to Throw One Away”. As the title implies, it suggests that one should throw away the first system and use the lessons learned to build the second, real system.
Why and how to enable ARM Thumb-2 instruction set in Yocto
The ARM Thumb-2 instruction set is not a new thing. In fact it was announced already in 2003. Yet, the standard ARM instruction set is often still used because it is the default option, while Thumb-2 could be a better alternative. This post explains why the Thumb-2 can be a better option for many applications and also how to configure it in Yocto build system for Linux kernel, system libraries, utilities and user binaries. Continue reading “Why and how to enable ARM Thumb-2 instruction set in Yocto”
Access hardware from userspace with mmap – Atmel SAMA5D3x programming mode case study
I was working with a device that used Atmel SAMA5D3x MCU. Sometimes the devices needed to be re-flashed which required putting the MCU to programming mode. However, the device enclosure needed to be opened and also a jumper wire was needed to do this. Then I realized that it would be possible to enter the programming mode directly from Linux by manipulating boot sequence controller registers in the MCU. Writing a dedicated device driver for this seemed like an overkill so I wrote a simple utility application with mmap instead.